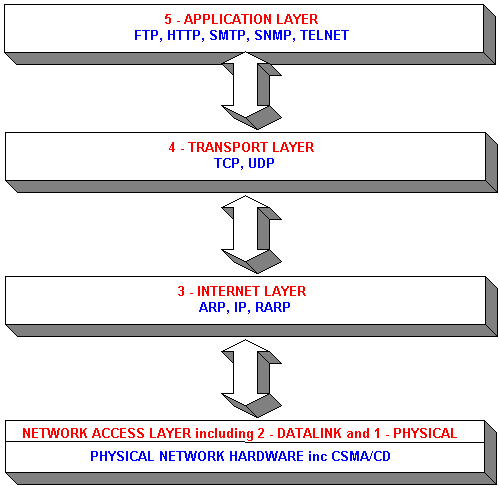
FTP was developed to allow reliable transfer of files across different platforms. To ensure reliability, FTP uses TCP at the transport layer. FTP provides simple commands and makes the differences in storage methods across networks transparent to the user. The FTP client is able to communicate with any FTP server, therefore the FTP server must also be able to communicate with any FTP client. FTP does not provide a user interface, but it does provide an application program interface (API) for file transfer. The client part of the protocol is known as FTP and the server part of the protocol is sometimes known as FTPd. The "d" suffix means Daemon - this is a legacy from Unix computing where a daemon is a piece of software running on a server that provides a service.
Different operating systems use different commands.
For example, in a DOS to Unix file transfer, DOS uses the "dir" command
to list the contents of the current directory. The FTP client translates
this to the "list" command which is transported across the network. A Unix
server does not recognise "list", so the FTP server has to translate "list"
into "ls", which the Unix machine understands. The Unix machine lists the
current directory, the FTPd transmits this as a "list" back across the
network and the FTP client translates the results into DOS format.
HTTP enables applications, such as browsers, to upload and download web pages. It uses TCP at the transport layer, again to ensure reliability. HTTP is a connectionless protocol that transmits a request, receives a response and then terminates the connection. HTTP transfers HTML (Hyper Text Markup Language) documents plus all of the other components supported within HTML - such as Javascript, Visualscript and applets.
SMTP transmits email, using TCP, to other computers that support the TCP/IP protocol suite. SMTP extends the local mail services that existed in the early years of LANs. It manages the transfer of email from the local mail host to a remote mail host, it is not responsible for accepting mail from local users or distributing received mail to recipients - this is the responsibilty of the local mail system.
SMTP uses TCP to establish a connection to the remote mail host, the mail is sent, any waiting mail is requested and then the connection is closed. SMTP can also return a forwarding address if the intended recipient no longer receives email at that destination. To enable mail to be transferred across differing systems, a mail gateway is used. A gateway exists at the University of Brighton to enable staff Macintosh machines to email students using the NT mailhost.
SNMP is a standardised protocol for the transort of network management information. Managed network devices can be interrogated by a computer running to return details about their status and level of activity. Monitoring software can also trigger alarms if certain performance criteria drop below acceptable limits. This protocol uses UDP at the transport layer. As discussed below, the use of UDP results in lower network traffic overheads. This is important when attempting to ascertain performance information - what use is a management protocol that dramatically increases network traffic load?
Telnet is a terminal emulating application program interface. It allows remote computers to connect to a server running Telnetd (the Telnet daemon). If the remote computer is not a dumb terminal (a terminal that has no processing power, just a keyboard and a screen), then Telnet convinces the server that it is. Telnet uses TCP for reliability.
TCP offers reliable, connection oriented transmission for upper layer protocols by establishing a connection between source and destination machines and terminating the connection when transmission is complete. The protocol offers data flow control, error checking of packets, acknowledgement of successful receipt of packets after error checking and packet sequencing. Those applications that do not require such a reliable, connection oriented service will use UDP.
In contrast to TCP, UDP provides an unreliable, connectionless service for upper layer protocols such as SNMP. The additional functionality of TCP is provided by a larger packet header than that required by UDP.
These two protocols resolve the differences in protocol suite layer addressing. There are two forms of addressing:
IP is used to provide the addressing functionality that is required to ensure packets reach their correct destination. All network devices should be uniquely identified by their IP address. If you are sitting at a networked Windows95 PC, goto the Run command from the Start menu and type winipcfg.exe - an IP Configuration window should appear. Amongst other things, it will tell you your interface card's IP address. As mentioned above, the IP address of a device is set by the network administrator. The IP address is used by routers to determine the best delivery path for each, individual, packet. IP is defined as an unreliable, connectionless protocol as it leaves resequencing and error checking of data to upper level protocols such as TCP. IP does not guarantee that packets will arrive at their destination in sequence, if at all.
Both physical media and CSMA/CD appear at the network access level. Strictly speaking, there are no protocols at this level - the physical media has its own specifications and CSMA/CD is really an access methodology operating at the datalink layer. Follow these links to media and medium access control.
Follow this link to the TCP/IP page and use its hyperlinks.