![]()
The OSI reference model is a hierarchical structure of seven layers that defines the requirements for communications between two computers. The model was defined by the International Standards Organisation. It was conceived to allow interoperability across the various platforms offered by vendors. The model allows all network elements to operate together, regardless of who built them. By the late 1970's, ISO was recommending the implementation of the OSI model as a networking standard, unfortunately, TCP/IP had been in use for years. TCP/IP was fundamental to ARPANET and the other networks that evolved into the Internet. Only a subset of the whole OSI model is used today. It is widely believed that much of the specification is too complicated and it's full functionality has taken too long to implement, although there are many people that strongly support the OSI model.
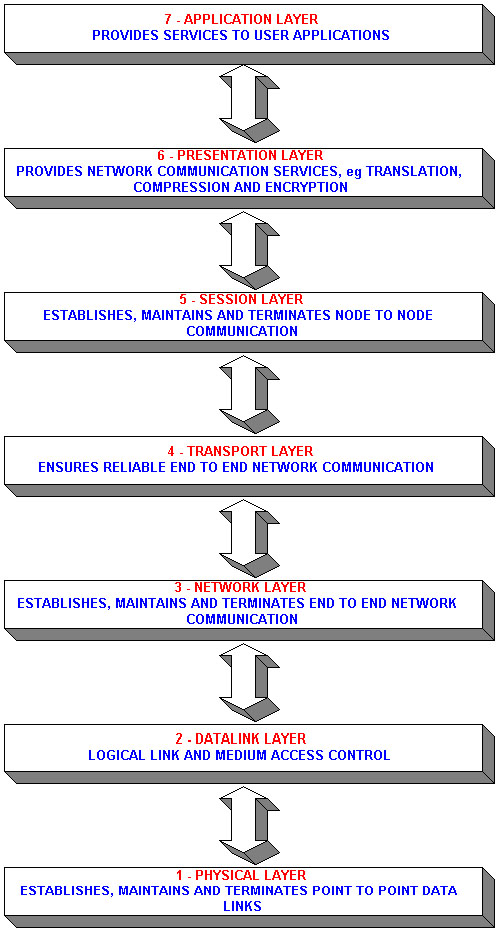
As data passes from an application and moves down the stack, each layer adds a header according to the protocol that exists at that layer. This is known as encapsulation. The only exception is the data link layer, a header and a trailer is added. After the data has been transmitted across whatever media is in use, the process of deencapsulation begins. Each layer of the stack, at the destination, removes the header (or header and trailer in the case of the data link layer) that was placed by its corresponding source layer. The physical and data link layers exist in hardware, all other layers are software driven.
This layer has protocols that support user applications, but it does not include the applications themselves. There is an opinion that the network operating system should be included in this layer, but this is open to disagreement. Strictly speaking, this layer deals with file access and management and includes the OSI X.400 and X.500 email protocols. X.400 allows interoperability between different email software and X.500 synchronises email across different systems.
The presentation layer protocols deal with data syntax during transfer between two application processes. If the client and server are using different file formats, this layer has conversion protocols. Therefore, computers using different file formats can still communicate with each other. Data encryption and decryption protocols also exist at the presentation layer.
Protocols at this layer are necessary for establishing, maintaining and ending sessions between user applications. Such protocols are designed to make the differences, across various platforms, transparent to the user.
Transport layer protocols are responsible for the reliability of end to end connections. These protocols assemble multiple network layer packets into a coherent message. This layer also provides flow-control and error recovery.
The network layer protocols establish, maintain and terminate end to end (network) links. These protocols route messages across the network(s) between two computers. Different network operating systems often have their own network layer protocols, but can also use other protocols. This flexibiltity is essential when communicating accross multiple client/server platforms.
Data link protocols provide logical link control and medium access control. These protocols provide reliability to the physical layer transmission by ordering the data into frames and adding error checking and addressing information. The network interface card assembles the data link layer frames.
Protocols at the physical layer are responsible
for establishing, maintaining and ending physical connections (point to
point) between computers. These protocols are manifested in the media across
which transmission occurs. These protocols do not specify the various cables
and connectors, these specifications are sometimes said to belong to layer
0.
| Business Direct Services' OSI page | Basic protocol information for each layer |
| Central Institute of Technology | General OSI model information |
| Cisco Introduction to Networking | OSI model overview |
| ISO/IEC 7498-1 : 1994(E) | Full listing from Peter McBrien's King's College page |
| Prof. John Larmouth's online OSI book | If it's not here, don't worry about it |